GRUB2: gaining root without a password
The problem
GRUB2, by default, does not protect against configuration changes.
To temporarily change the default GRUB2 configuration, you:
- Power on the machine
- Continouosly tap the ESC key (or maybe hold down the Shift key)
- Get to the GRUB2 screen
- Press “e”
The exploit(s)
As you can imagine, modifying the boot options used is not ideal. For starters, someone could boot a malicious USB drive (if Secure Boot is enabled) and do all sort of bad stuff.
The easiest method to gain control of the machine, however, is by directly booting into a BASH shell. This is done by hijacking the init process and replacing it with the path to the shell, i.e. /bin/bash:
- Power on the machine
- Continouosly tap the ESC key
- Get to the GRUB2 screen
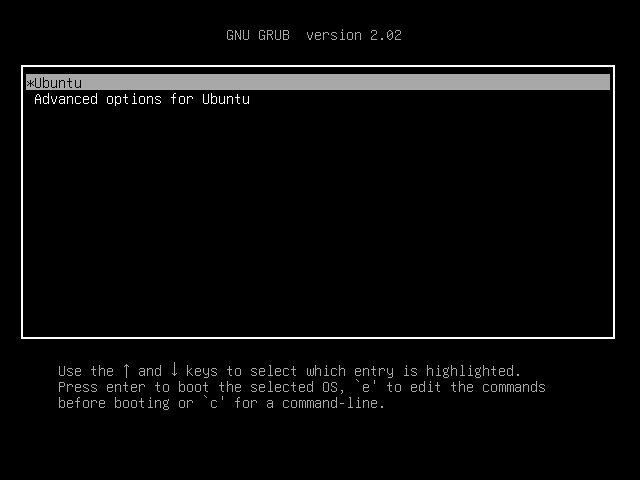
- Press “e”
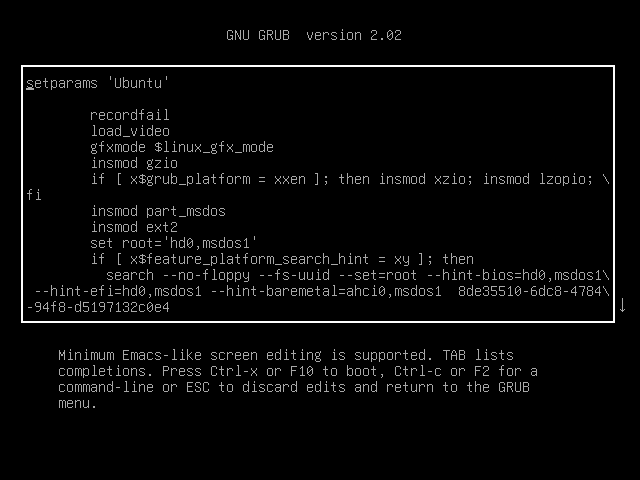
- Find the line starting with “linux”
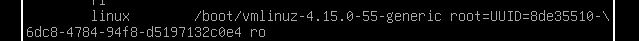
- Append
init=/bin/bash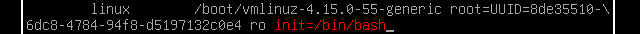
- Press Ctrl+x or F10 to boot
Shutting down
After booting, you might’ve tried to shut down or reboot the machine, only to see a message similar to the following:
System has not been booted with systemd as init system (PID 1).
This happens because init is supposed to take care of shutting down or rebooting the system. However, we have hijacked it and made it /bin/bash, so what if you can’t find the power button, or are working remotely?
The fast and easy fix is to press or send the key combination of Ctrl+Alt+Del, this will immediately shut down (or reboot, depending on the configuration) the machine.
The solution
To fix this, there is, generally speaking, only one reliable solution: setting a password for editing the configuration.
You might also want to disable the recovery boot option by editing /etc/default/grub and setting GRUB_DISABLE_RECOVERY=true.
Setting a password:
https://wiki.archlinux.org/title/GRUB/Tips_and_tricks#Password_protection_of_GRUB_menu